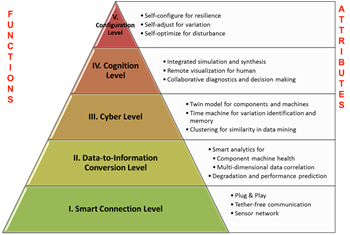
What You Can Expect In 2017 For IOT
When you look at expert predictions for what will happen in the IoT space in 2017, it is clear technologies and thinking is both advancing quickly. It is also clear that traditional industries and brands face challenges from nimbler newcomers, with some of those...
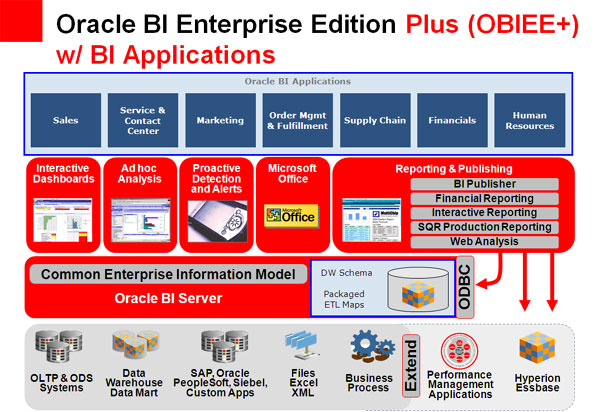
Oracle Looks at EPM Trends
No branch of business operations has been more thoroughly transformed by the computer age than finance, the original "data-driven" business discipline. Successive technology revolutions have given rise to Enterprise Performance Management (EPM) solutions that seek to...

Ignore Bad Data… Sort Of
In George Orwell's classic Animal Farm there is a well-known quote that sums up the issues tackled in the book: "All animals are equal, but some animals are more equal than others". In terms of data, this is a truism: all data is equal, but some data is more equal...
Security and Compliance Concerns in the Cloud
A Rackspace study shows that resilience and security will remain top motivations for businesses moving into the cloud throughout 2016. While cost is always a major factor, in a poll of 500 UK IT and business decision makers, resilience, disaster recovery, and security...
Five IoT predictions for 2016
The Internet of Things (IoT) has been discussed for many years, but it still seems to be falling short of its potential. It seems that this year, the promise of software sitting inside a wider variety of devices is set to open up new revenue streams. Device...
How to Fix Mobile BI
With the advent of big data, business intelligence has again been pushed to the forefront of IT's attention. With so many organizations conducting more and more business on the move, mobile devices have been looked to as the answer. That said, the lackluster nature of...
Secure Network Access for Personal Devices
The smartphone phenomenon has reached global proportions, and every day more and more people are expecting to be able to access work materials from their own devices. In fact, almost half of companies now allow employees to use their personal devices to access the...
Location Based Intelligence Software
Using maps to present data is hardly a new phenomenon. Even modern Geographic Information Systems (GIS) have been around for decades, albeit in their own little bubble. These systems, while incredibly useful, required special training and were rarely used outside of...
Data Loss Prevention
In spite of the big headlines about external hacks or insider attacks leading to data loss, it is true that most of the corporate data that gets exposed is through messaging systems. Employees accidentally sending out confidential information through email, instant...
Data Masking
In the modern world of financial services, the protection of your customer's data is critical. Not only critical for your company's reputation but to avoid a whole host of legal and financial obligations should a data breach ever happen. Encryption is one way of...
Protecting Your Mobile Data
According to some studies, over two-thirds of lost smart phones contain sensitive or confidential business information. This can lead to, sometimes serious, breaches of data and confidentiality. With the increasing use of mobile hardware in businesses – whether this...
Is RBAC Dead
For many years one of the easiest ways to control access to data has been through the use of roles. Each user in an organization was traditionally assigned a 'role' by IT security and this role determined the amount of information and level of access granted to the...