Digital Transformation for Power Plant
Picture by Timothy Cheng, GE Reports Power system equipment condition monitoring is a must if you wish to ensure the efficiency and reliability of electricity supply. This is typically achieved with equipment maintenance or replacement based on typical service life...

Pushing Limits Of Analytics With IoT
Introduction The traditional method of analyzing data once it has been collected and saved is no longer fit for purpose. Today's technology requires data analysis while it is being created, while it is being transferred from one device to another, and while it is at...
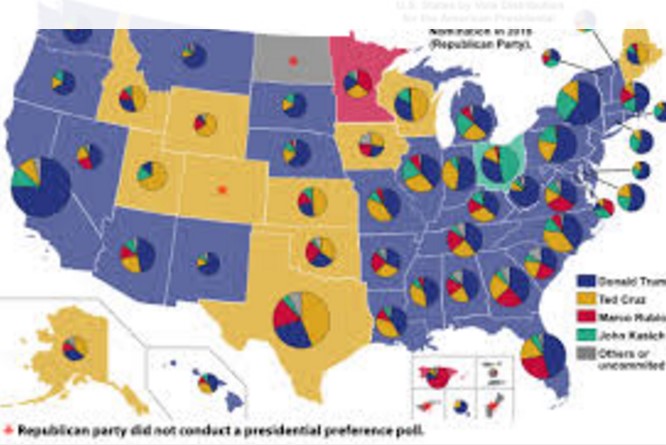
Why Polling Prediction Failed – Data Quality
In the modern world, data and information are driving forces of any business or operation. Poor data analysis can lead to unfortunate circumstances for any company or public organization. We only need to look at the latest election to see how false data collection and...
The Rise of Impersonator Bots-DDoS
Distributed Denial of Service attacks are on the rise. At best it might mean your website is unavailable for a couple of hours. At worst, the most malicious can cost companies thousands upon thousands of dollars. Ofer Gayer, a security researcher writing for...
Don’t Neglect Data Relevance
It is okay to have incomplete or inaccurate data in your system. That’s a statement that would make many business executives shudder. But in a sense it is true – a focus on accuracy and completeness without also looking at relevance can result in very unhelpful...
Past, Present & Future of BI Performance
Improved business performance has been a promise of business intelligence gathering since forever. However it is in the last two decades that the technologies and processes have progressed to a point where they are genuinely beginning to help. While the advances in...
Big Data Trends in Business Intelligence
In the fast evolving and fast improving world of business analytics, big data has an increasing role to play in making intelligent business decisions. But not only is the role big data plays in your business intelligence analytics increasing, but so is the data...
A 50-billion Device Security Headache
With the huge growth in mundane devices, everything from fridges to light bulbs, being connected and integrated with each other in the new 'Internet of Things' (IoT), the scope for hackers has grown right alongside with it. The new network has undoubtedly many useful...
Rise in Big Data Analytics Spending Plans
2015 is really the year that big data analytics is coming of age. Louis Columbus, writing in Forbes about the recent IDG Enterprise study, “2015 Big Data and Analytics, Insights Into Initiatives and Strategies Driving Data Investments,” provides us with some startling...
Succes of IAM
Identity and access management (IAM) is the cornerstone of cyber security when it comes to people and systems. It ensures that only approved people can access certain resources and systems. But what happens when you add the myriad of devices that are set to become...
The K.I.S.S Principle
The temptation with business intelligence, and especially with the amount of real-time information now present in the modern age, is the tendency to too much. However this excess of real-time data, far from giving us a complete view of a developing situation, can...
DDoS: Most Important Hacker Tool in 2015
The Internet is undoubtedly one of the greatest technological gifts humanity has ever seen. It has transformed society and the way we look at the world and communicate with each other; it's been a boon to commerce and business. All of this is balanced, however, by the...